Dante
Over the last two weeks, I finally completed the Dante ProLab. which focuses on red team operations. This lab simulates a real company network. Each machine had a purpose and taught me many things.
The lab consists of 14 Windows and Linux machines with a total of 27 flags. The large number of machines gave me hands on experience in Pivoting, Enumeration, Privilege Escalation and Web Exploitation
🕵️♂️ Enumeration
I think this is the most important stage for every individual machine you will be attacking. It is very easy to skip a small detail that will often be important later on. Do not rush through things as this will only make you waste more time in the end. Keep an excel sheet or a notebook to write down details, credentials or users you found, you never know when a password might be reused. I also strongly suggest to keep track of which flags you have found and on which machine, as of now the lab does not tell you where each flag is located so if you skip one you may have to search every machine. It is also nice to keep track of which machines you have already pwned and how they interleave with each other. A key detail is that most machines are independent, that is, you should be able to solve them without any previous information that you gain from pwning other machines. Some machines, on the other hand, are dependent and you will only be able to solve them once you pivot, or gain credentials.
🌐 Web Exploitation
Dante contains some web exploitation where classic vulnerabilities have to be exploited to gain a foothold to a machine. For the most part, these exploits are very simple. I think the hardest part was to use information that was previously enumerated to our advantage to perform these exploits. Dante will contain a variety of vulnerabilities such as: LFI, RCE, and exploiting publicly known CVEs.
⚡ Privilege Escalation
I found that most of the privilege escalations were pretty trivial. I definitely spent longer trying to get a foothold for most machines. I would say that the hardest ones were the buffer overflow exploits, but this depends on your experience, I personally have never had to perform a buffer overflow so I found them pretty challenging. I would also like to suggest to perform post-exploitation recon, this is because there are many hints, or notes that are left behind in some directories that are only readable by the Admin or Root user.
🔀 Pivoting & Lateral Movement
Only one machine is accessible through the initial network, to gain access to the machines inside the Dante network you will need to pivot. I used ligolo as it makes this step extremely easy, this tool allows you to double pivot and forward ports without much complexity. Dante also focuses on lateral movement teaching you that to compromise an entire network the path is not straightforward and you may have to move laterally to gain more information before advancing. 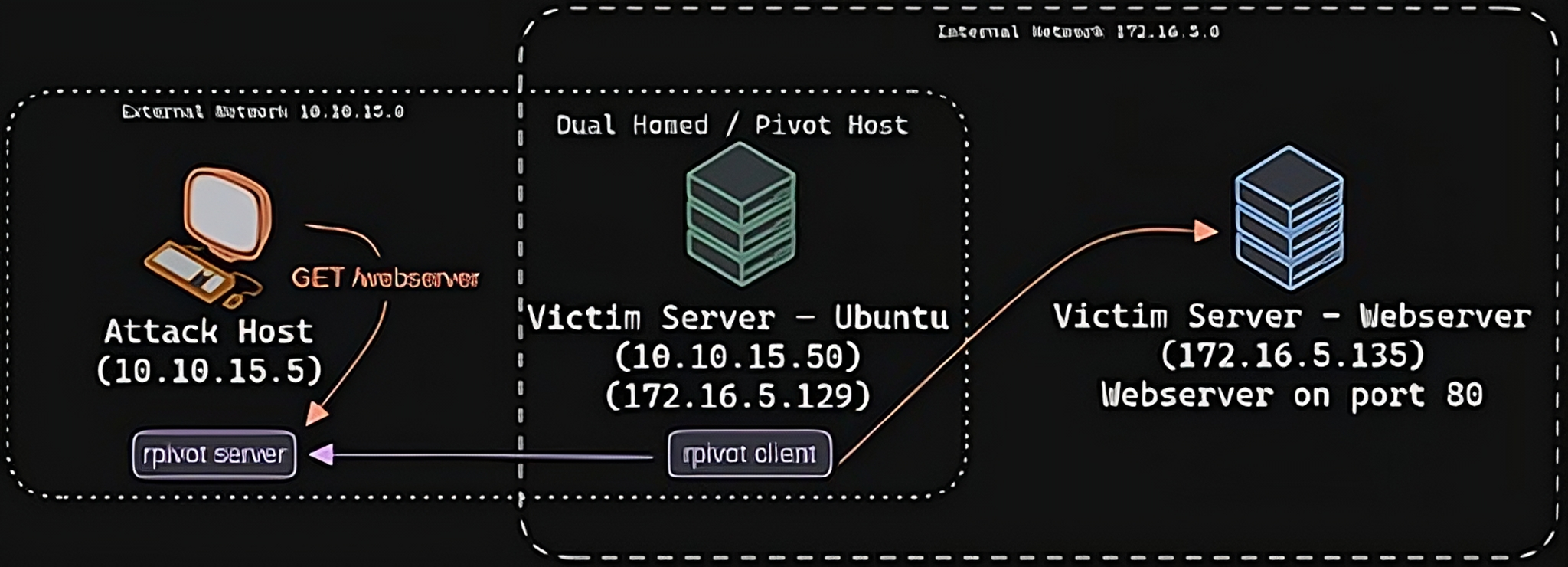
💡 Tips
I leave below some tips to complete this lab