Delivery
Delivery is an easy Linux machine. An initial port scan reveals three tcp ports open. Port 80 has a website running which directs us to an OSTicket instance. After sending a ticket we are given a valid company email address from which we can view the ticket, this is used to create a user in the mattermost instance running on port 8065. Going over to one of the text channels we can see some information by the root user which lets us into the box. Following this we find an sql server which has the credentials to access it in cleartext. Inside the database we can find root’s password which we can crack with the information we found in the mattermost chat.
Enumeration
Nmap
After running a basic nmap scan we can see that there are three open TCP ports. Port 8065 is unknown and there is not a lof of info about it online, for now our only entry point is the website on port 80.
1
2
3
4
5
6
7
8
9
10
11
12
cat nmap/allports
# Nmap 7.94SVN scan initiated Sat Apr 19 12:46:49 2025 as: nmap -Pn -n --min-rate 5000 -p- -oN nmap/allports 10.10.10.222
Nmap scan report for 10.10.10.222
Host is up (0.013s latency).
Not shown: 65532 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
8065/tcp open unknown
# Nmap done at Sat Apr 19 12:47:03 2025 -- 1 IP address (1 host up) scanned in 13.52 seconds
We can verify that the website is a simple html page by gong over to http://10.10.10.222/index.html and verifying that it loads. The website has a Contact Us link. This page now shows the following text:
1
2
3
4
5
## Contact Us
For unregistered users, please use our [HelpDesk](http://helpdesk.delivery.htb) to get in touch
with our team. Once you have an @delivery.htb email address, you'll be able to have
access to our [MatterMost server](http://delivery.htb:8065).
Mattermost
Before going over to any of these pages we must add delivery.htb and helpdesk.delivery.htb to our hosts file. http://delivery.htb:8065 is running a MatterMost instance. Since we have no login credentials I tried creating a user, but only emails with a hostname of delivery.htb are allowed. Since we do not have any, I change my focus to the helpdesk site which is running osTicket.
osTicket
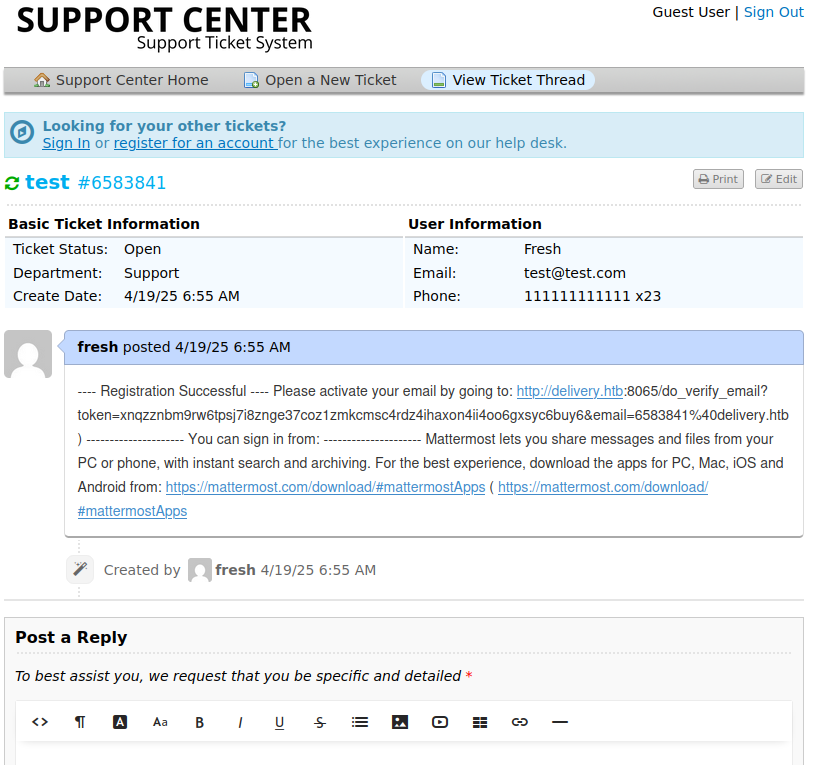
After creating a random ticket we are given an email address and ticket ID number which we can use to view our ticket. Most notably the email that we were provided has the format of ID@delivery.htb. After this I created an account in the Mattermost page we saw earlier. Before being able to register the new user we have to confirm it with our email address. Going back to osTicket we can view our ticket which shows that we got the verification email.
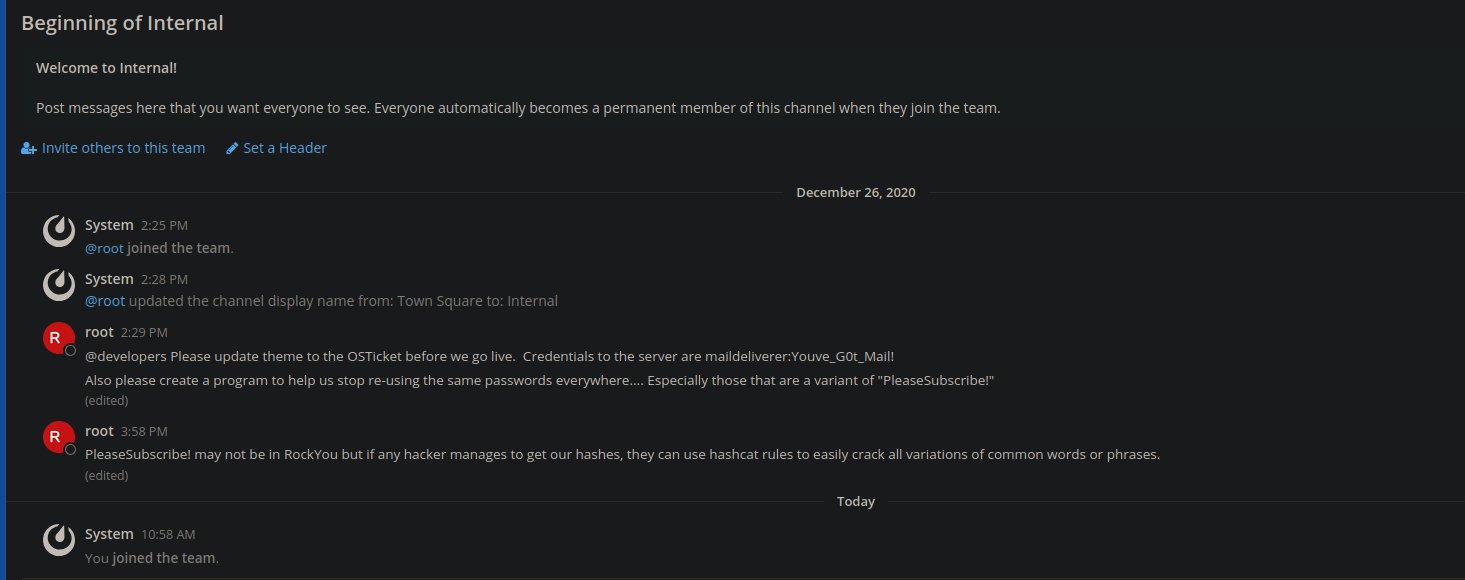
By clicking the link we can activate our account and we are allowed into the Mattermost server. We can see that it has one channel with the name internal. This channel has a lot of information about the server and the password format they use:
Gaining access to the machine
We now have some information to go by, one set of credentials: maildeliverer:Youve_G0t_Mail and that the server uses variations of the words PleaseSubscribe! as passwords. I actually spent a bit of time here, I did not realize we could simply login to the machine with ssh with the provided credentials. I instead used these credentials to login into the osTicket instance as an administrator from which I could reveal the version being used in hopes of finding a known exploit to get a reverse shell. I did find that the version being used was v1.15.1 which does not have any RCE vulnerabilities. Looking at the dashboard shows all the sent tickets. Which did not contain any useful information.
After gaining access to the machine with the provided credentials we are logged in as the user maildeliverer their home directory was empty and we did not have any sudo rights or any setuid binaries that we could use to escalate our privileges. I did see that port 3306 was open which meant that there was an sql database running. Which could contain the hashes root was talking about in the messages sent over Mattermost. I ran linpeas to make sure I was not missing anything obvious. Linpeas showed that there was a mattermost installation inside the /opt directory. After some googling I found that Mattermost uses a database to store information I also saw a post asking for Mattermost to not store the database credentials in cleartext. After some digging I found the credentials inside /opt/Mattermost/config/config.json
1
2
3
4
5
6
7
8
9
10
11
12
13
"SqlSettings": {
"DriverName": "mysql",
"DataSource": "mmuser:Crack_The_MM_Admin_PW@tcp(127.0.0.1:3306)/mattermost?charset=utf8mb4,utf8\u0026readTimeout=30s\u0026writeTimeout=30s",
"DataSourceReplicas": [],
"DataSourceSearchReplicas": [],
"MaxIdleConns": 20,
"ConnMaxLifetimeMilliseconds": 3600000,
"MaxOpenConns": 300,
"Trace": false,
"AtRestEncryptKey": "n5uax3d4f919obtsp1pw1k5xetq1enez",
"QueryTimeout": 30,
"DisableDatabaseSearch": false
}
Accessing the Database
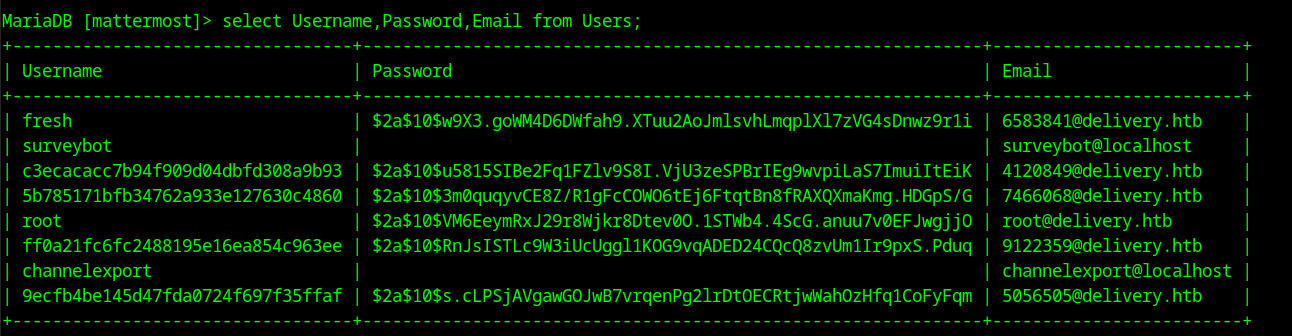
We can see that the sql instance is running on port 3306 and has the database mattermost. We also have a set of credentials to access it: mmuser:Crack_The_MM_Admin_PW. After using the following command mysql -u mmuser -p mattermost mySQL asks us for the password which we have. After inputting it we gain access to the data inside the database. This database has a table for user information. We can view the table schema with the command describe Users. The table contains a username, email and password field, we can use the following command to view its contents: SELECT Username,Password,Email FROM Users;
Cracking the Password for Root
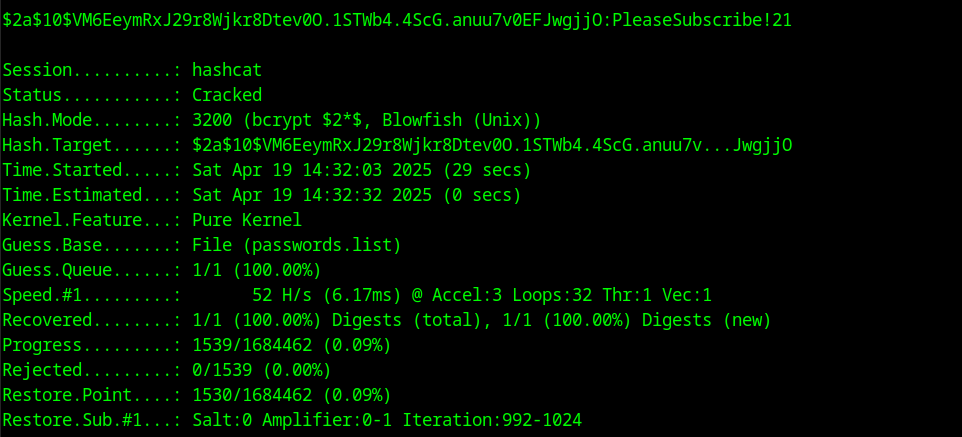
We can see that the passwords are hashed but most importantly we have the password for the root user. We could try cracking the hash with rockyou.txt but this will not work because the password is some variation of the words PleaseSubscribe! root already has told us that it is not in rockyou so we must create our own wordlist. To do this I used hashcat rules to produce variations of the original version. I used the following command to do so: hashcat --stdout password.txt -r /usr/share/hashcat/rules/dive.rule > wordlist.txt this command creates a wordlist and outputs the contents to wordlist.txt. We can begin cracking the password with the following command:
1
hashcat hash.txt wordlist.txt -m 3200
We use mode 3200 because its a bcrypt password. The hash cracks almost immediately and we can see that the password for the root user is PleaseSubscribe!21.
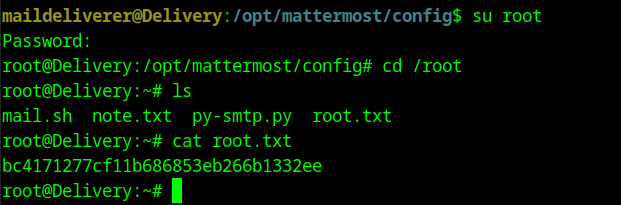
We can now do a simple su root to login as the root user when prompted for the password we can use the password we just cracked. We get root access and we can read the root flag.